CVE-2019-19908
Recently x00pwn, a few others from the InfoSec-Prep Discord server, and myself have been participating in a challenge we dubbed “The 12 Days of CVE-mas.” The premise of the challenge is to use the free time we have this holiday season to discover and develop as many exploits as possible, in the hopes of obtaining CVE(s).
Up until this point we had found quite a few local denial of service exploits as well as SEH overwrites, but few of them were worth developing or reporting.
Additionally, local buffer overflows and DoS exploits rarely get assigned CVEs as they must be performed locally.
phpMyChat-Plus 1.98
Today, as I was going through the list of programs we had identified for fuzzing, I came across phpMyChat-Plus 1.98. I became interested as I saw it was a recently maintained program (with the most recent version having been released 2 weeks ago) and it also utilized a backend database of MySQL.
Installing the app locally, I began setting it up and before I had completed the installation I discovered the first vulnerability.
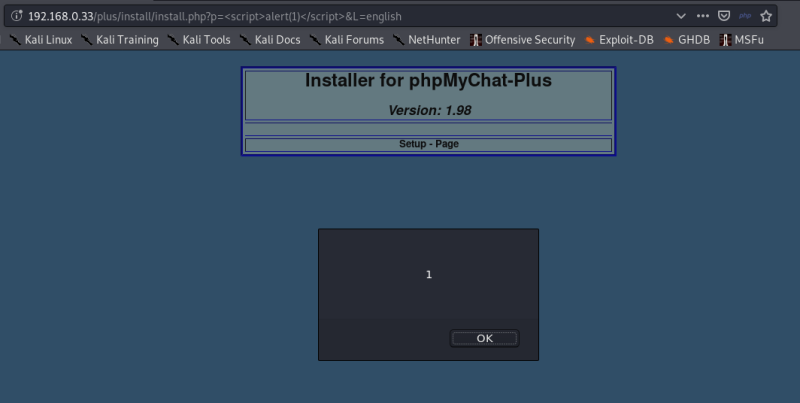
Figure 1: install.php parameter ‘p=’ vulnerable to reflected XSS
It is one of x00pwn’s philosophies that in applications where one vulnerability exists, many more often exist. Thus, I knew if I kept digging post-installation, I would be sure to find more.
Unbeknownst to me at this time, this application has a history of vulnerabilities, but luckily none overlap with my next discovery.
Quite by accident I messed up the installation; as I attempted to reset the admin account password, I noticed that the username one entered to reset was also present in the URL. It is often an indicator of reflected XSS when a URL parameter changes what is displayed on the page.
Steps to Obtain Reflected XSS
Starting URL:
http://localhost/plus/pass_reset.php?L=english&pmc_username=admin&LIMIT=1
Visiting this page displays ‘admin’ in the username field.
Payload:
"><script>alert(1)</script>
Looking through the page’s source code, I saw it was necessary to close the current tags to escape the username field. This is done with the "> part of the payload; now we are free to inject JavaScript code.
Payload + URL:
http://localhost/plus/pass_reset.php?L=english&pmc_username="><script>alert(1)</script>
Putting the two parts together we get this.
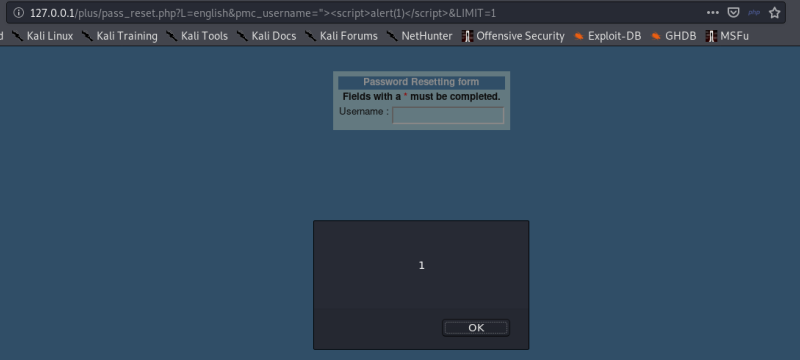
Figure 2: pass_reset.php parameter ‘pmc_username=’ vulnerable to reflected XSS
Since this XSS can be achieved without authentication, and I was eager to obtain my first CVE, I decided to report this vulnerability to both the developer and MITRE.
My experience with MITRE was very pleasant and I included a link to a real-world website running this program with the payload so they could confirm its presence. Within just 1 hour I was assigned CVE-2019-19908.
Speedy response time
While this is not a groundbreaking discovery, I am certainly proud as it is my first CVE.
The Exploit-DB submission is currently pending.


